concept
Due to the communication of all hosts that support TCP / IP protocols, they must pass the IP layer, so the security of the IP layer is equivalent to providing the entire network. The basis of secure communication. Given that IPv4 is still very broad, it has also added support for IPv4 in the formulation of IPSec. The initial set of IPsec standards were developed by IETF in 1995, but since there were some unresolved problems, ITF has launched a new round of IPSec development work, as of November 1998, has basically Develop completion. However, this new agreement still has some problems, and it is expected that the IETF will carry out the revision of the next round of IPsec in the near future.
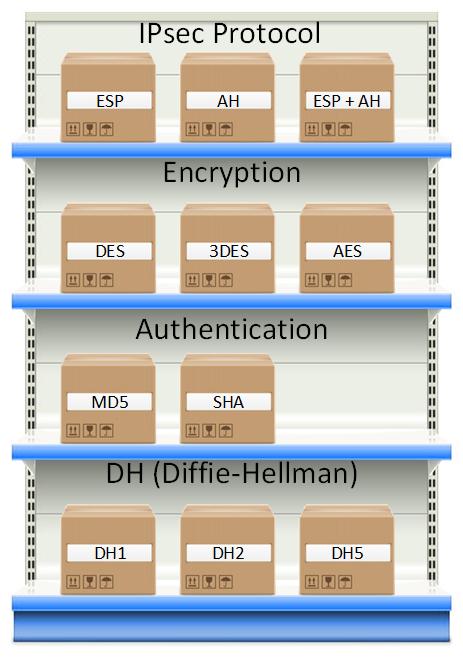
IPsec provides two security mechanisms: authentication (AH) and encryption (using IPsec ESP).
• The authentication mechanism enables the data receiver of IP communication to confirm the true identity of the data sender, and whether the data is tampered with during transmission.
· Encryption mechanism ensures the confidentiality of the data to prevent data to be eavesdropped during transmission.
Explanation
IPsec main function is encryption and authentication, in order to encrypt and authenticate, IPSec also requires a key to manage and exchange for encryption and authentication. The key is managed and manages the use of the key. The above three aspects are specified by AH, ESP, and IKE (Internet Key Exchange, Internet Key Exchange). In order to introduce these three protocol, you need to introduce a very important term SA (Security Association security association). The so-called security association refers to a "connection" between the security service and the carrier it serves. AH and ESP need to use SA, and the main function of IKE is the establishment and maintenance of SA. To implement AH and ESP, you must provide support for SA. If the communication is used to establish a secure transmission path with IPSec, it is necessary to negotiate the security policy to be used in advance, including the encryption algorithm, key, and key of the key, and so on. When the security strategy used by the two parties, we will say that both parties have established a SA. SA is a simple connection that provides some IPsec security to the data transfer thereto, which can be provided by AH or ESP. When a given SA is given, the processing of IPSec is executed, such as encryption, authentication, etc. The SA can be combined in two ways, which is a proximity and nested tunnel, respectively.
IPsec's working principle is similar to the bag filter firewall, which can be seen as an extension of the package filtration firewall. When a IP packet is received, the package filter firewall uses its head in a rule table. When a matching rule is found, the package filter firewall will process the received IP packets in accordance with the method developed in this rule. There are only two types of processing here: discard or forward. IPSec determines the processing of the received IP packet by querying the SPD (Security Policy Database Security Strategy). However, IPsec is different from the package filtration firewall, and the processing method for IP packets is discarded, and there is one, which is directly forwarded, that is, IPSEC processing. It is this newly added processing method to provide further network security than package filtration firewalls. Perform IPSec processing means encryption and authentication of IP packets. The filtered firewall can only control the passage of the IP packet from or to a site, you can reject the IP packet from an external site to access some sites, or reject an internal site to certain external websites. access. However, the package filter firewall cannot guarantee that the packets from the internal network are not intercept, and the packets entering the internal network have not been tampered with. Only after encryption and authentication of the IP packet is implemented, the confidentiality, authenticity, integrity of the data packets transmitted outside the external network can be guaranteed to be possible to secure communication through the Internet. IPsec can only be encrypted or only authenticated, or only both IP packets can also be implemented. But whether it is encrypted or certified, IPsec has two working modes, one is a tunnel mode, and the other is the transmission mode.
